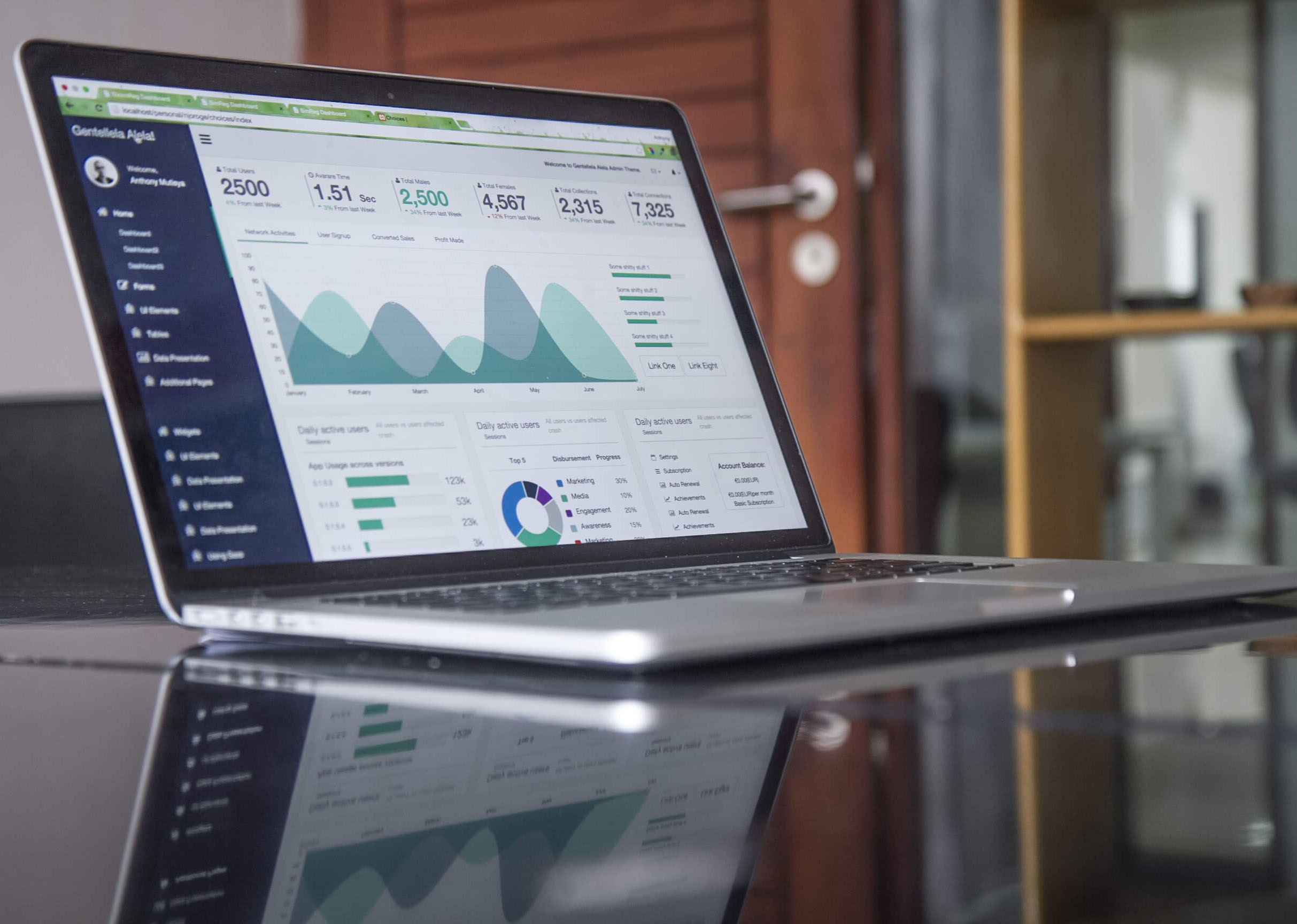
Intrusion Campaigns
Scheduled intrusion campaign simulation within an organization. Planning of attack vectors to evaluate the level of cyber resilience (risk management) and threat detection in a target organization. Simulation of Spear Phishing, SMS Spoofing, SPAM, DDoS, infected USB drives, etc.
Precise planning excluding personnel and teams, where the client receives attack information in real-time to assess their organization’s response. Evaluation reports and recommendations.
Real Assessment
Analyze organizational behavior in a simulated real attack.




Attack Simulation
Conducting a scheduled attack simulation is the best way to measure your company’s cybersecurity level.
- Evaluation of awareness and protection levels
- Personnel and senior management awareness
- Implementation of new security measures
Cyber Resilience Evaluation
Periodic evaluation of cyber resilience levels within a business organization.
- Social Engineering Attack.
- Technical Attack.
- DDoS Attack.
- Table Top Approach

Attack Planning
Scope Definition
Attack Execution
Real-Time Report (RT)